Why frontline businesses love Beekeeper
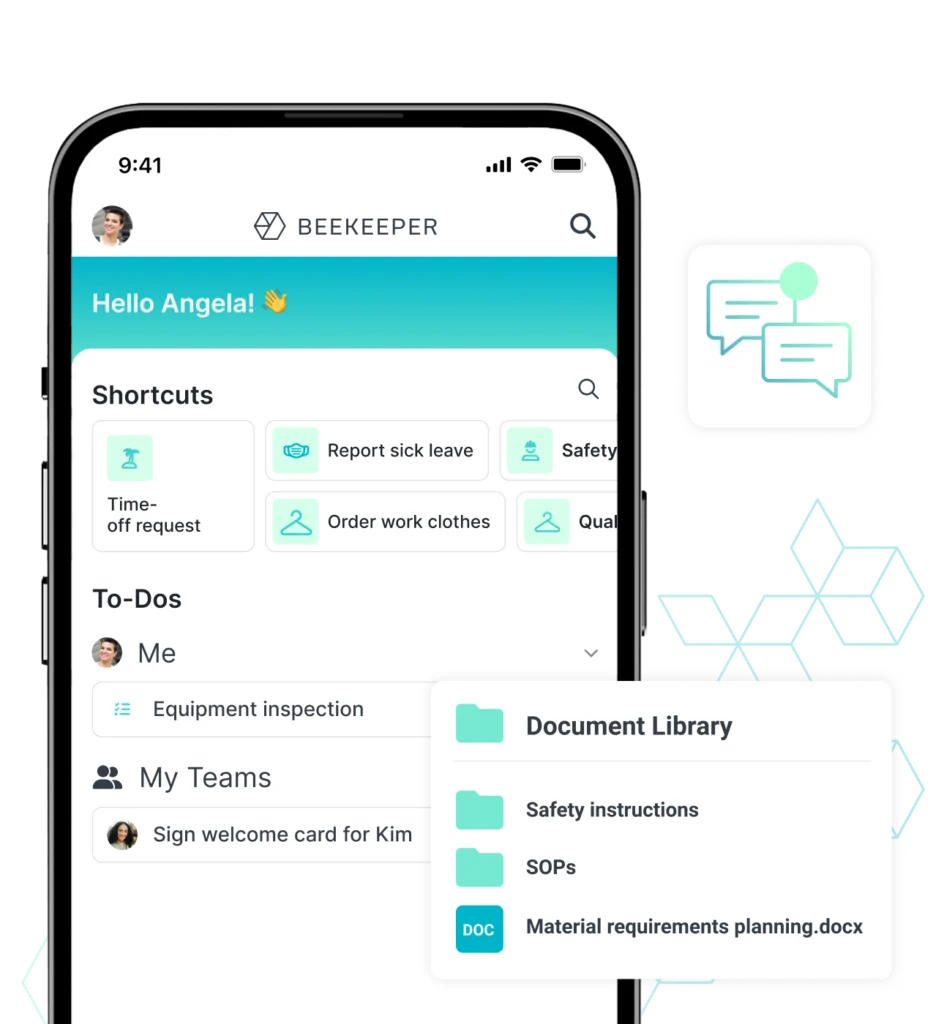
Making frontline lives easier
Stay informed and connected
Beekeeper connects frontline workers directly to company news, critical updates, and real-time chats, ensuring they feel informed, valued, and part of the team — no matter where they work.

Reduce managers’ admin work

Focus on people, not paperwork

Drive bottom-line impact

Your roadmap to frontline success
Partner with Beekeeper to transform your frontline with a proven framework implemented by thousands of customers. While every company’s path is unique, we guide you through each stage to success, driving engagement, boosting productivity, and creating lasting business impact.
Connect
Start with connection
Begin your journey by bringing communication and access directly to the frontline with a tool they’ll actually use and love. Beekeeper empowers, engages, and unifies your workforce.
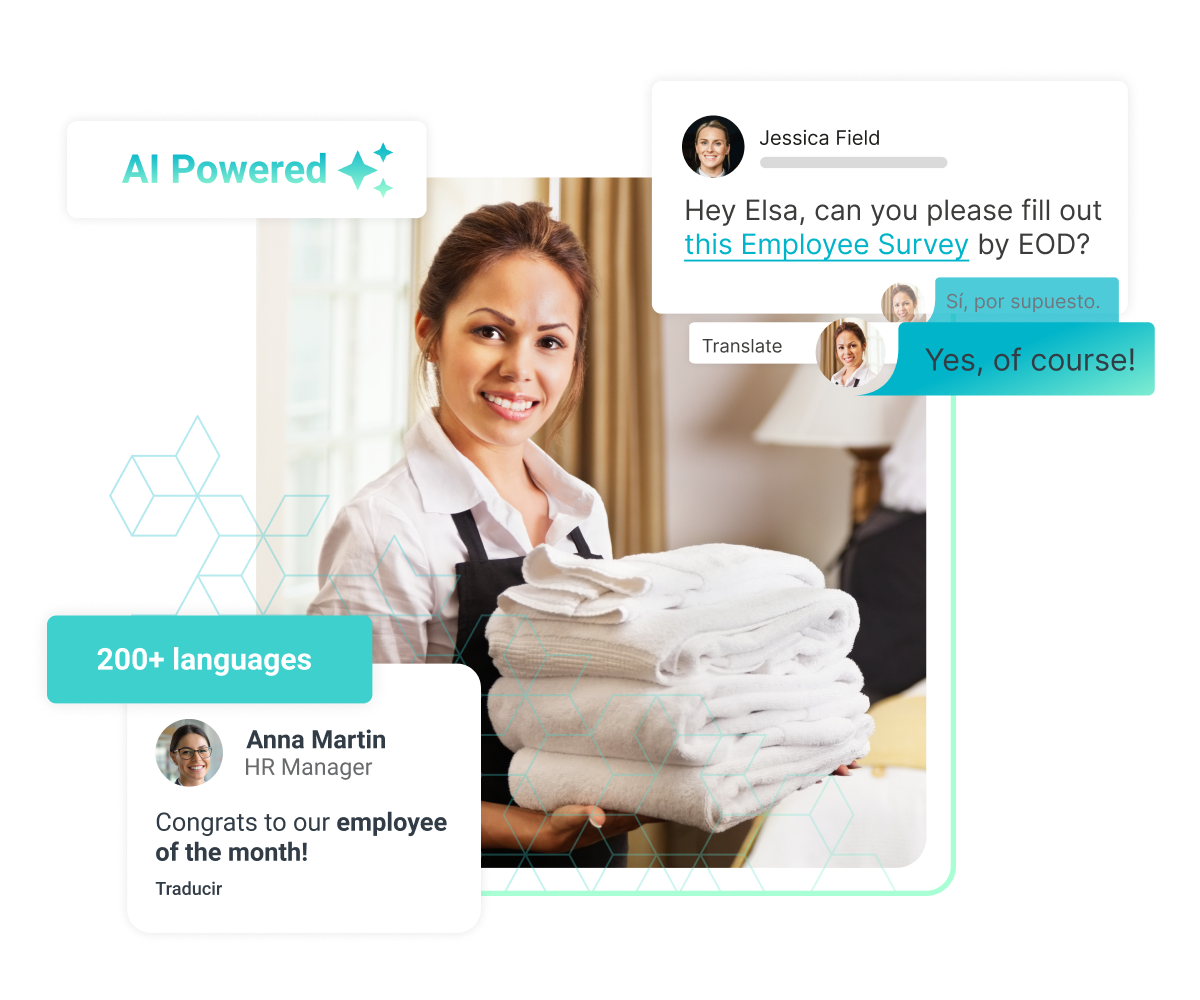
Integrate

Simplify
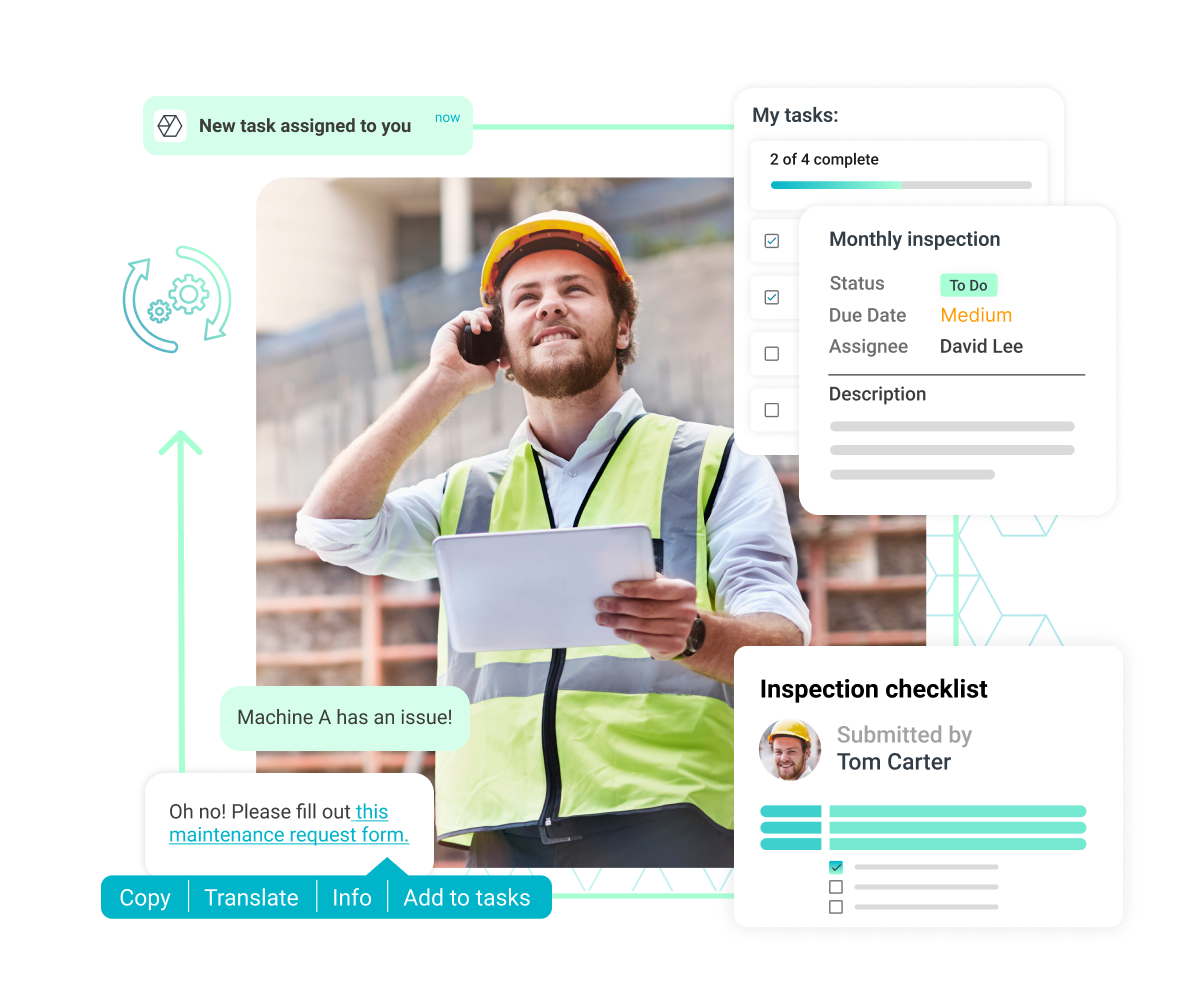
Accelerate
Frontline industries run on Beekeeper
Hospitality

Elevate guest experiences by keeping hospitality teams connected with real-time updates and task coordination across shifts.
Retail

Enhance store operations, improve the associate experience, and empower retail teams to provide exceptional customer service.
Manufacturing

Keep factory teams informed and connected to reduce turnover, avoid production delays, and improve workplace safety.
Construction

Enable real-time communication across job sites for safer, more efficient crews — and more projects delivered on time.
Healthcare

Engage and empower frontline healthcare workers to increase retention, improve patient care, and support compliance.
Key resource
Fuel your frontline: A buyer’s guide for internal communications software
An in-depth look at Beekeeper’s features and the key factors you need to consider before deciding on an internal communication tool for your frontline team.

Explore more
Ready to get started with Beekeeper?
Join 1200+ companies transforming frontline work with Beekeeper. Start your journey today to make every task easier, every team stronger, and every shift smoother.